Connecting Azure Functions with Azure App Configuration

Assuming that you require your application that lives on an Azure compute fabric (App Service, Azure Functions, Azure Container Apps, Azure Kubernetes Service) to connect to a managed and centralised store for app settings/configs, then the Azure App Configuration service helps in this direction. The use of Microsoft Entra ID through managed identities makes life easier without exposing credentials within your app repository or within CI/CD tools. Let's see how we do this.
Create Azure App Configuration Service
Using the Azure CLI:
az login
az appconfig create --resource-group [yourRGName] --name [instanceName] --location [azureLocation] --sku FreeThis should get you a Free to use Azure App Configuration Service
Set values in Azure App Configuration
Next set some values in you App Config Store for the needs of your application(s). In your Azure App Configuration instance in Azure, go to Create>Key-value:
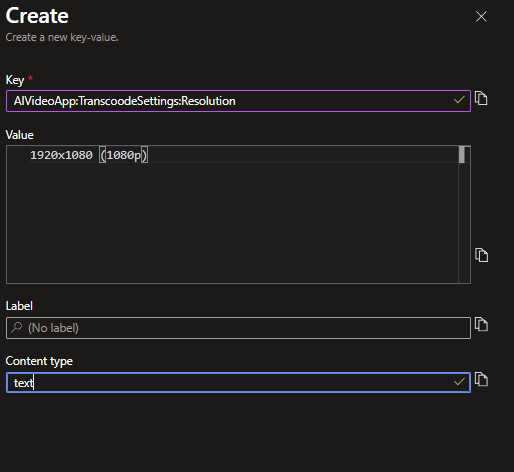
Note that the guidance for setting your configs is that it follows the format [ApplicationName:Section:SettingName] as observed above for the Key item, and then your desired value for your Value item.
Apply code for reading App Configuration
The base code for accessing a value in App configuration is as follows where we will also assume that we will be authenticating into the service via Microsoft EntraID (more on this later on):
Install the necessary packages
nuget install Microsoft.Azure.AppConfiguration.AspNetCore
nuget install Azure.IdentityRequired Nuget Packages
Access Azure Config entries
var builder = new ConfigurationBuilder();
builder.AddAzureAppConfiguration(options =>
{
string endpoint = "[your_configApp_endpoint]";
options.Connect(new Uri(endpoint), new DefaultAzureCredential());//using EntraID
});
var config = builder.Build();
//utilise your app config setting as the following
Console.WriteLine(config["AIVideoApp:TranscoodeSettings:Resolution"]);Access Azure App Configuration
With this baseline code, you can deploy your application when you are ready. But after deployment there are further steps needed to make sure the application (now in Azure) has the correct access permissions to read fetch values from the
Assign ManagedIdentity and Assign RBAC Role
Now that you have your application in Azure, we will need to set a ManagedIdentity on the accessing entity, plus assign the "App Configuration Data Reader Role" (which is enough for reading values, nothing more).
For an Azure Function, you can do this in the Portal or the CLI. For the Portal for an Azure Function, you can go to the Function instance, Settings>Identity. The turn ON the System assigned Identity. This means that your Azure Resource (in this case a Function, could have been an App Service too) has an identifiable ID within Microsoft EntraID that can be used for accessing other permissioned resources such as Azure App Configuration.
Assign RBAC Role to your resource
Then, go to the Azure App Configuration instance specifically, Access Control (IAM), Add > Add Role Assignment. Now search for "App Configuration Data Reader":
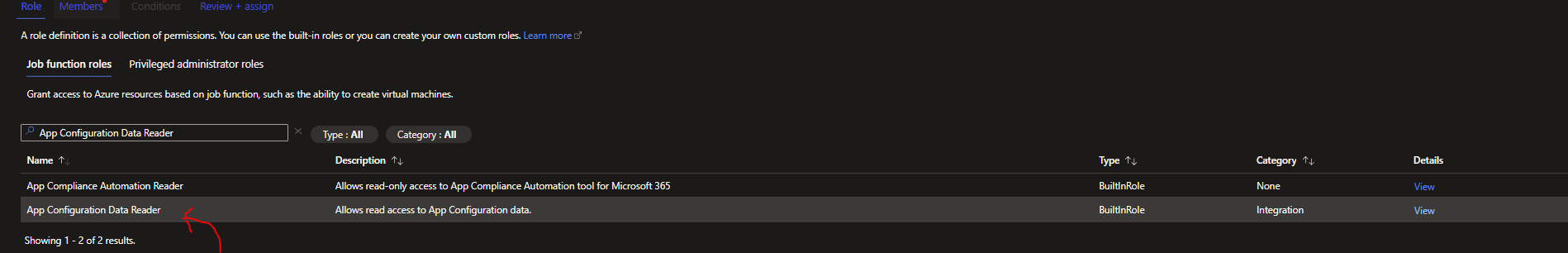
Select "App Configuration Data Reader" here and then click Next.
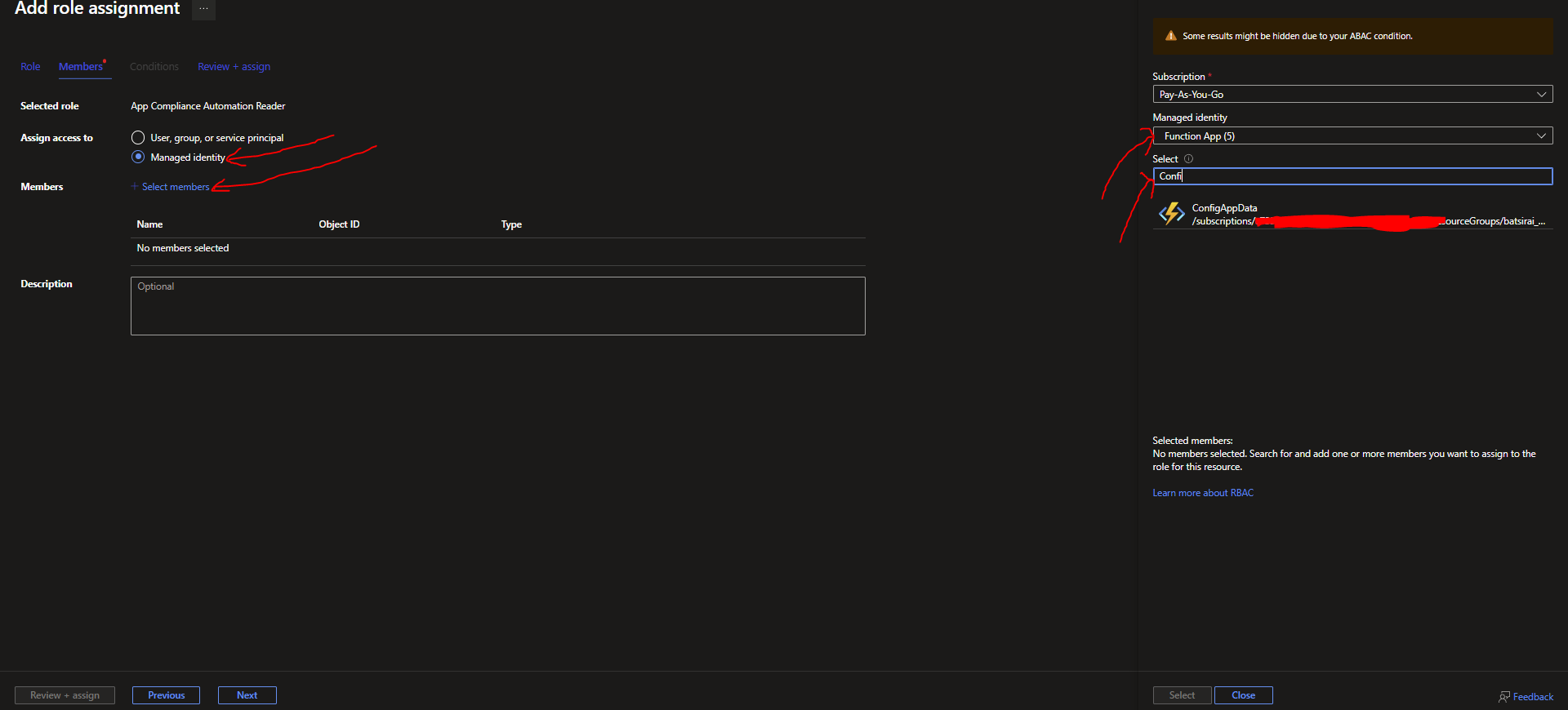
On the next screen, select Managed Identity > Select Members and choose your Application from the right hand panel (based on the application type - Functions, App Service etc..). Make sure you select the correct instance of your resource where you deployed our code/are going to be deploying code to. In this case I am choosing Functions and selecting/searching for my target Function app:
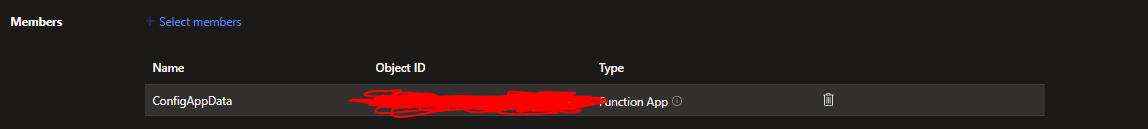
After selecting, your app should appear in the list on the Members section:
Click Review + Assign ... then Click Review + Assign once more to confirm the details 😄.
To confirm the assignment, the Azure Function should appear in the Role assignments on the App Configuration Resource with the role labelled correctly:
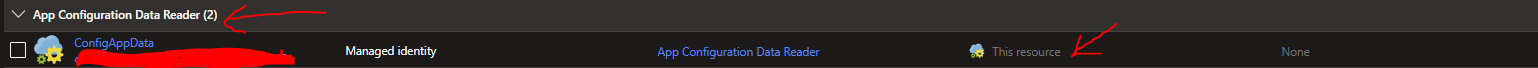
That's it!!! Your application code will now be able to access values from Azure App Configuration so long as the referenced values exist. You may require restarting/refreshing your application after the role assignment is complete.
