Azure Kubernetes Service Entra ID with Kubernetes RBAC

Should the default Authentication and Authorisation method for an AKS Cluster be modified from "Local Accounts with Kubernetes RBAC" to "Entra ID authentication with Kubernetes RBAC" , it is often the case that the individual user is unable to access any resources within the AKS Cluster at that point - Namespaces , Services, Ingresses, Workloads and Pods.
The issue
What is likely to be seen is this error screen:
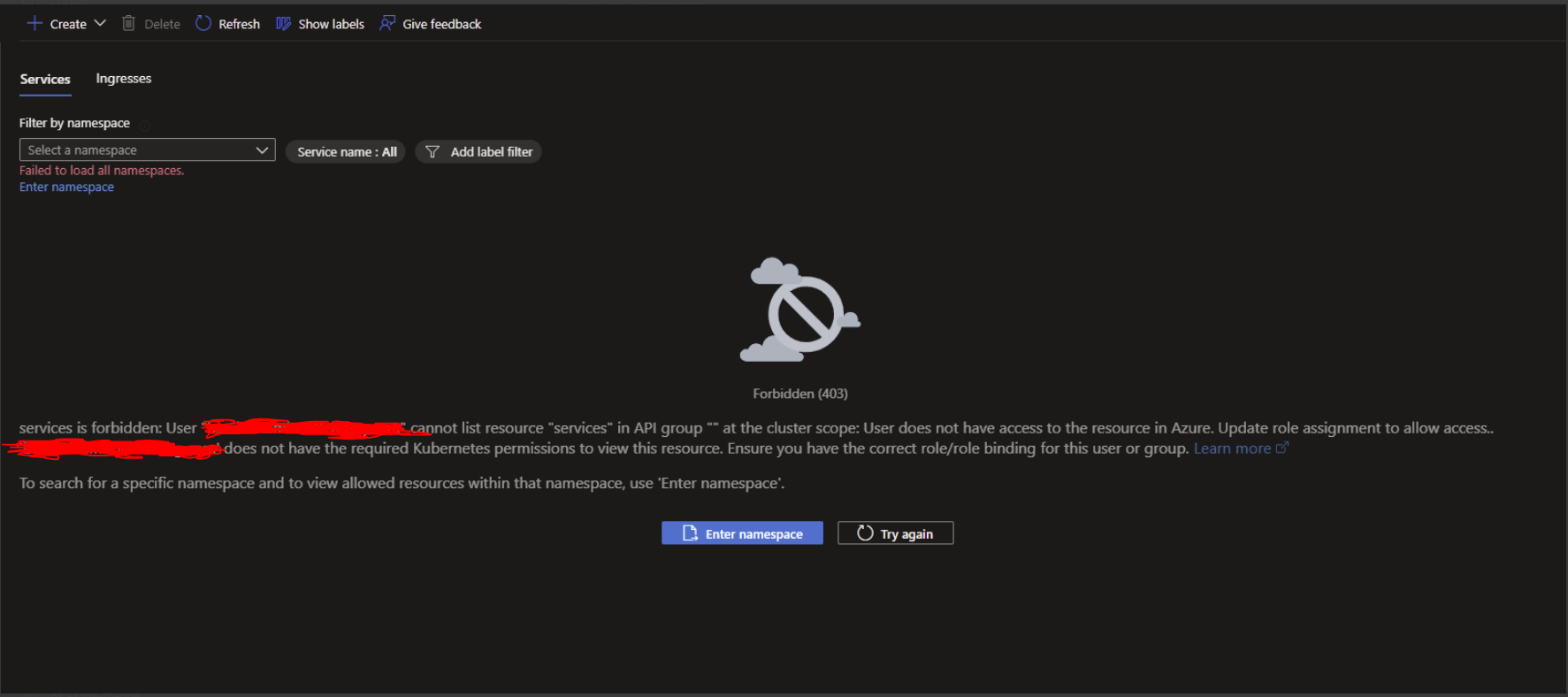
The issue is that the user does not have required role assignment in order to view the Kubernetes cluster resources. Or so it appears.... At this point the user it is now assumed that user should authenticate and authorise into the AKS cluster via Microsoft Entra ID with Kubernetes RBAC. Let's keep the last part (Kubernetes RBAC) handy for now.
The Solution
The solution is NOT to be attempting to give elevated roles to the particular user such as Azure Kubernetes Cluster Admin or Owner with the IAM settings of the AKS Cluster in hopes of simply using a god-mode to break through this permissions barrier.
Rather the user in this scenario requires an assignment to an Entra ID group first, where the user is an assigned member of that EntraID Group. This addition of the user can be done in either EntraID Admin Center or within the Azure Portal from an instance of EntraId
Then finally, this target group that should have a GUID must be added as group that will have a cluster-admin ClusterRole binding for the AKS cluster. In order to do this, we can use the Azure CLI with the following command:
az aks update --resource-group [resoruce_group]--name [aks_instance_name] --aad-admin-group-object-ids [your_entraId_group_guid] --aad-tenant-id [your_tenant_id]Assign EntraID to AKS for ClusterRoleBinding
This update may take a while to update on the AKS Cluster. The update should see the following result within the AKS Security Configuration Settings
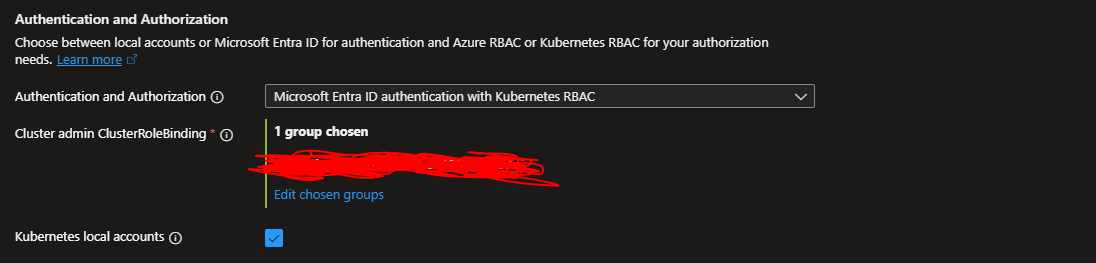
Because this process uses Kubernetes RBAC as we mentioned specifically, the auth and authentication cannot be resolved through IAM tooling and assigning roles there. If we had been using EntraID authentication with Azure RBAC, then the process would have used just the following example command without any entraId group assignments in Admin Center:
az aks update --enable-azure-rbacAzure RBAC enablement on AKS
For Azure RBAC authentication, AKS will use a webhook to find out and evaluate the Azure Role Assignments for Kubernetes Resources.
